Google Drive Spam Abuse
Google is the trendsetter in the email filtering and adoption of novel features that reduce the spam amount.

May 11, 2020
Google's contribution to spam and malware fights is undisputable. Without doubts, we can say that Google is the trendsetter in the email filtering and adoption of novel features that reduce the spam amount. On the other hand, the spammers are trying to find their way around the solid service base and abuse the services in various stages of spam delivery. Today, we will take a look at how Google Drive is abused in the spam campaigns.
At Virusfree.cz, we have observed the Google Drive links contained within the spam messages between February 18th, 2020, and April 8th, 2020. We've recorded 30 861 807 unique emails containing 1 958 unique Google Drive links, these were sent from 48 341 unique IP addresses. Also, we've tried to request all the individual files the links point to, in most of the cases the files were the presentation files that contained just one slide with the image and URL link. If you want to read about the link analysis, please, follow this link.
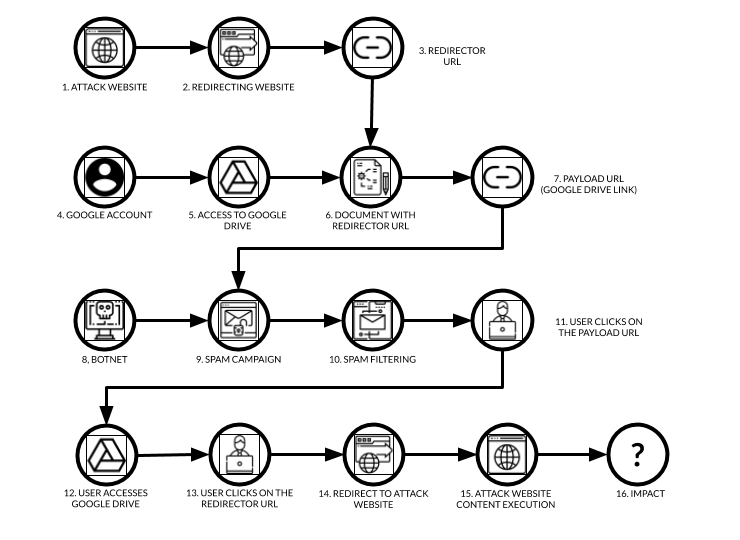
The number of unique Google Drive links is low but there are considerable complications for the attacker when abusing Google services. The attackers leverage this by the amount of the sent spam messages with Google Drive link. The image below shows how such an attack works.
Stage 1
The attackers need to prepare the attack website (1), the one where that will be executed in the user's browser. Attackers do not expose this website directly mostly because the domain or the hosting represents an important asset where more campaigns and other attack activities join. Therefore the attackers set one or more redirecting websites (2) and create the redirector URL (3). There are three types of redirection: using a URL shortener (and the attackers avoid Google shortener, for obvious reasons) or hijacked or hacked websites or attacker’s dedicated redirecting services (own or rented).
Stage 2
At this stage, the attackers need a working Google account (4) using which they will access the Google Drive service (5). The account may be created on purpose but we believe some of the accounts used for this type of abuse were hijacked. In Google Drive, a document is created (6) with a teasing image or text, and hyperlink leading to the redirector URL (3), and it is shared. The link then leads to a particular document located on Google Drive and is being used as the payload URL (7) in the next stage of the attack.
Stage 3
Now the attackers need to have a botnet (8) capable of spamming. As mentioned before, we’ve recorded 48 341 unique IP addresses trying to deliver the spam messages with the payload URL (7). The number is not high therefore we believe the attackers rent the botnet. Spam messages in the campaign (9) are usually very simple and the spam filter (10) should detect the campaign.
Here lies the explanation of why the attackers use Google Drive links. Many companies simply whitelist all emails containing links pointing to online services from vendors with a higher reputation regardless of the sender (email or IP) because their internal users use online file sharing service to share internal documents, others may be the customers and blacklisting would disrupt the service usage completely.
Now when the email is delivered to the user's mailbox, the user needs to click (11) on the delivered payload URL (7) in the message body. When this happens, a Google document opens from Google Drive (12) with the teasing image or text asking the user to click on another link (13), this time it is the redirector URL (3). Finally, the redirector URL leads to the attack website (14) which content is executed in the user’s browser (15). As the final impact (16) we usually see pharmacy spam, phishing, malware, or practically any type of email related threat.
Conclusion
These scenarios are quite widespread. The abuse at scale does not affect only Google service however it is one of the most abused services. At Virusfree.cz we are recording also the links pointing to Microsoft services, Dropbox, and other vendors of these services. User interaction is still required but the popularity of these attacks shows that they are most likely successful.
If you would like to have access to the threat data such as a list of URLs delivered by the botnets or full access to our RBL (listing currently more than 13M of IP addresses), feel free to contact us.